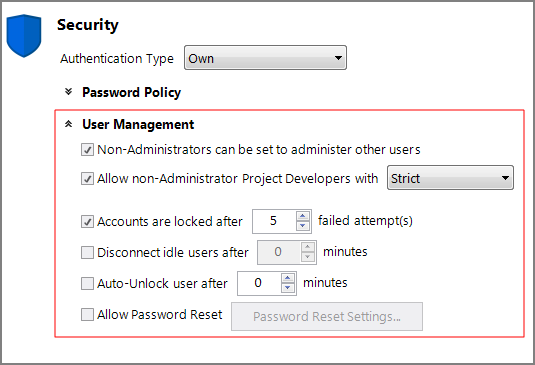
By using DiveLine server-level security settings, you can specify user password and connection settings and control users' abilities to manage other users and their access to advanced development features. These settings are found under the Security section of the Server Settings > General tab (Tools > Server Settings > General > Security > ![]() User Management).
User Management).
Click the expand chevron to display these security settings.
The security settings consist of the following:
-
Non-Administrators can be set to administer other users—Set to allow non-administrator users to administer other users or groups. After this is set and saved, you can set the Owned By field on the Security/Licensing tab for each user's account (see User Edit Tabs) and the General tab of the group's account. The users named in the Owned By field become sub-administrators and can perform the following administrative tasks:
-
Change user attributes of users they own.
-
Add or delete users from groups they own.
-
Use proxy logon for users they own when in clients such as DivePort and ProDiver. Proxy logons are useful when you wish to test that your access settings for the user or group is behaving as intended.
-
Update assigned values for existing properties for a user or group they own.
 NOTE
NOTE
-
-
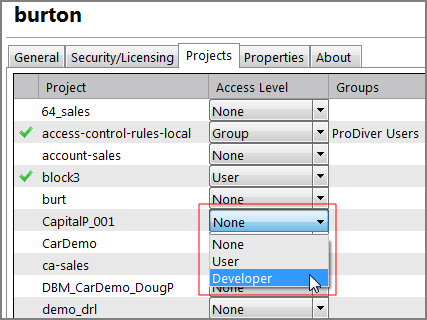
Allow non-Administrator Project Developers with <restrictions>—Set to allow developer project level controls on the DiveLine server. When you select this option, you can control Project Developer access on a project-by-project basis by means of an Access Level drop-down choice (None/User/Developer) on the user's
 Projects tab. Project Developer restrictions, at the server level, can be set to Strict or Casual.
Projects tab. Project Developer restrictions, at the server level, can be set to Strict or Casual.Project developers have limited access to the DiveLine:
-
Can open Workbench, but can only see the projects where they are set as developers.
-
Must be set to Developer in the Clients list on their Security/Licensing tab.
 NOTE
NOTE -
Have full read/write access to all files within the given project.
-
Can set Production script schedules for Production scripts within the projects where they are set as developers.
 NOTE
NOTE -
Cannot access the DiveLine server's Server Settings or any project aliases.
The project access level applies not only to Workbench, but to other clients such as ProDiver and DivePort. The following restrictions apply to users with Developer access:
-
Strict (recommended)—The Strict choice does not allow project developers to run Execute nodes in Production scripts or Execute process objects in Integrator scripts by including a -disable_execute parameter. This parameter does not apply to Tunnel scripts.
 NOTE
NOTE -
Casual (use with caution)—The Casual choice does allow project developers to run Execute nodes in Production scripts and Execute process objects in Integrator scripts. Use caution when using the Casual choice because users could gain inappropriate access to data.
-
None (default when this option is not checked)—Non-administrative DiveLine users are rejected when they attempt to log into Workbench.
See Projects in the topic User Edit Tabs.
-
-
Accounts are locked after X failed attempt(s)—Set the number of failed logon attempts that are permitted before the account is locked. This setting is not applicable when the Authentication type is Web Server.
-
Disconnect idle users after X minutes—Set the number of minutes a user can remain idle before being disconnected.
-
Auto-Unlock user after X minutes—Set the number of minutes a user account remains locked before a reset (not applicable to Web Server authentication).
-
Allow Password Reset—Set to configure a Forgot Your Password? link to appear on the DivePort logon screen. This setting is only valid when the Authenticate Type is Own. (See Password Reset Settings).